Offensive Shifts, Offensive Policies: Cybersecurity Trends in the Government-Private Sector Relationship - Canadian Global Affairs Institute
Future Internet | Free Full-Text | Adversarial Machine Learning Attacks against Intrusion Detection Systems: A Survey on Strategies and Defense
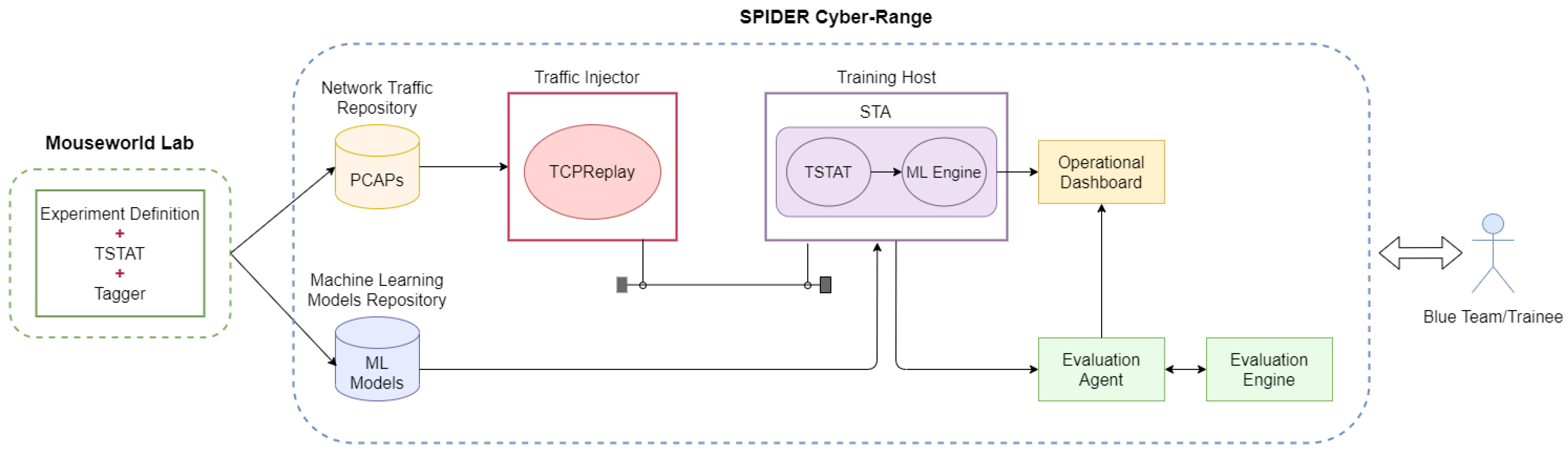
Applied Sciences | Free Full-Text | Integration of Machine Learning-Based Attack Detectors into Defensive Exercises of a 5G Cyber Range

Cyber Operations: Building, Defending, and Attacking Modern Computer Networks: O'Leary, Mike: 9781484242933: Amazon.com: Books

Cyber Operations: Building, Defending, and Attacking Modern Computer Networks: O'Leary, Mike: 9781484242933: Amazon.com: Books

Cyber Operations Building, Defending, and Attacking Modern Computer Networks ( PDFDrive )-507-563 - Studocu
Read PDF Cyber Operations: Building, Defending, and Attacking Modern Computer Networks: 2015 > QBOGDXWQ8HOW

Cyber Operations: Building, Defending, and Attacking Modern Computer Networks, Second Edition Book - EVERYONE - Skillsoft

Cyber attacks are rewriting the 'rules' of modern warfare – and we aren't prepared for the consequences

Cyber Operations: Building, Defending, and Attacking Modern Computer Networks: O'Leary, Mike: 9781484242933: Amazon.com: Books

Cyber Operations: Building, Defending, and Attacking Modern Computer Networks: O'Leary, Mike: 9781484204580: Amazon.com: Books

Forget a Whole-of-Government Cybersecurity Strategy—It's Time for a Whole-of-Nation Approach - Modern War Institute

Cyber Operations: Building, Defending, and Attacking Modern Computer Networks: O'Leary, Mike: 9781484242933: Amazon.com: Books

Electronics | Free Full-Text | A Comprehensive Review of Cyber Security Vulnerabilities, Threats, Attacks, and Solutions

مشخصات، قیمت و خرید کتاب Cyber Operations: Building, Defending, and Attacking Modern Computer Networks اثر Mike O'Leary انتشارات مؤلفین طلایی | دیجیکالا