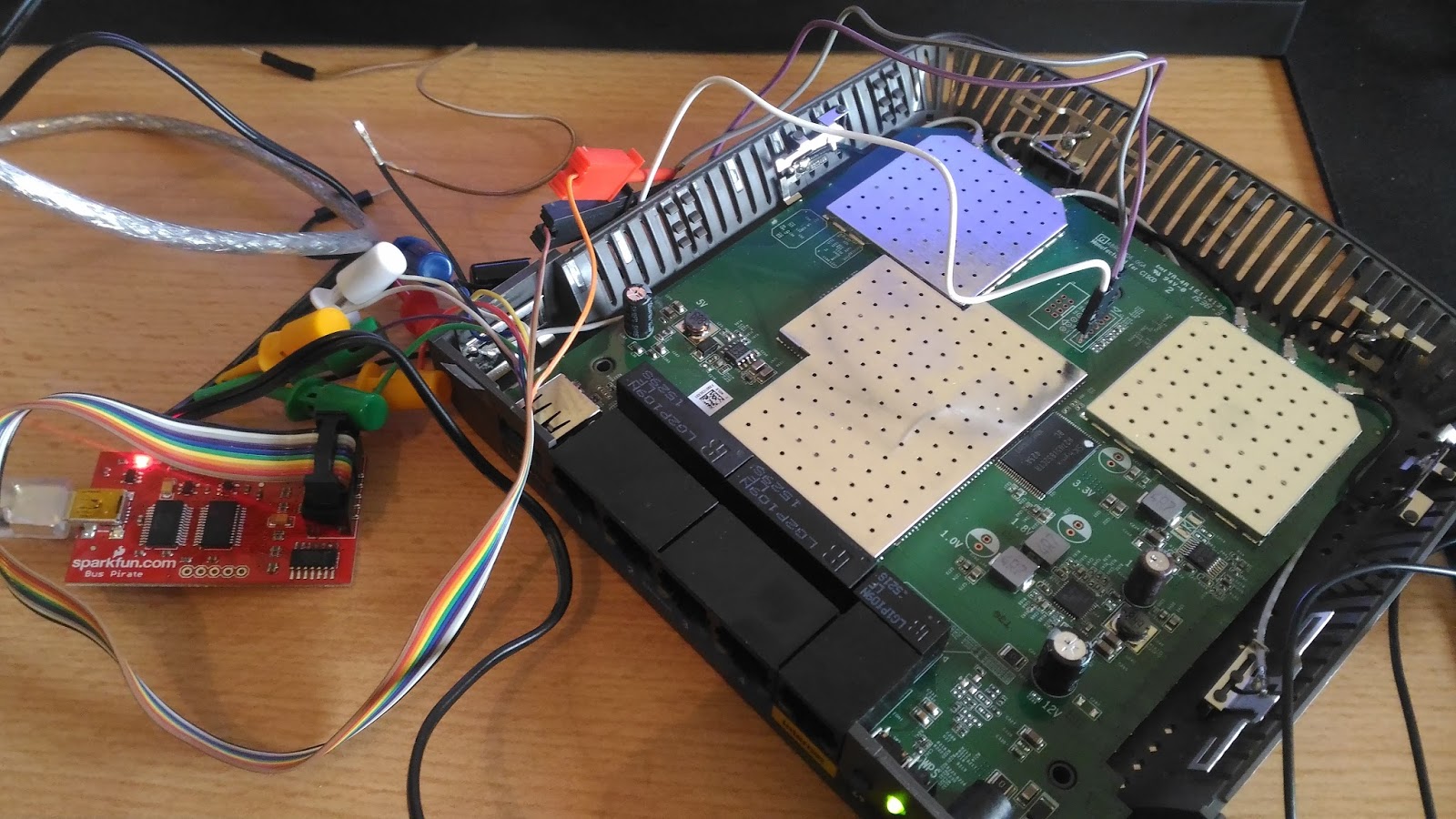
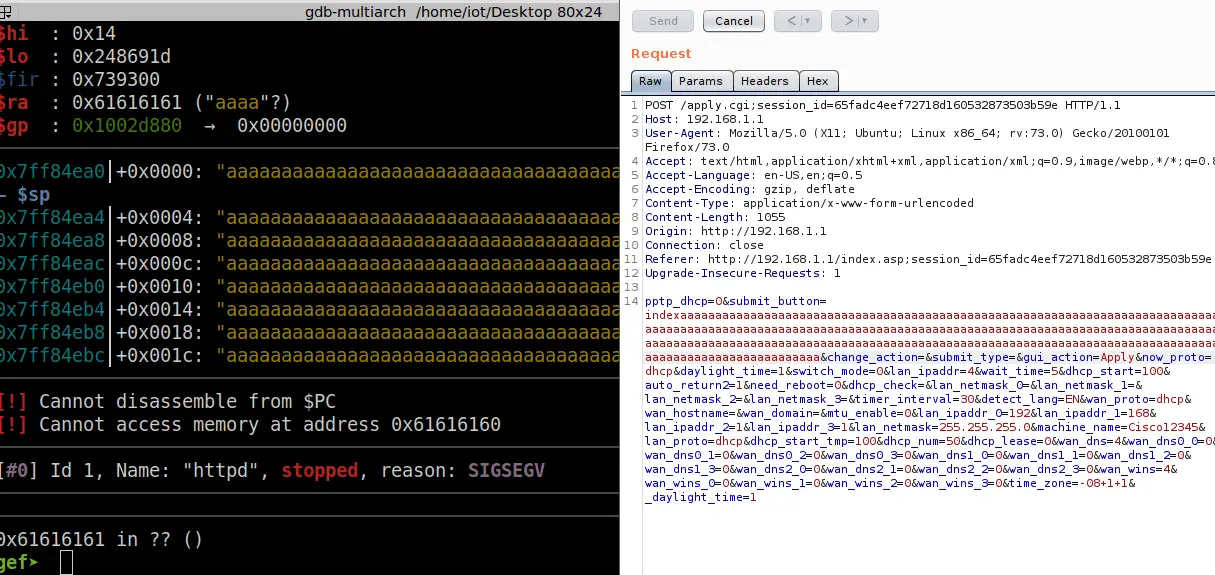
Wireless Network Security Breach - Wi-Fi Protected Setup (WPS Bug) PIN Brute Force Vulnerability - Reaver - TCP Port 32764 Back Door

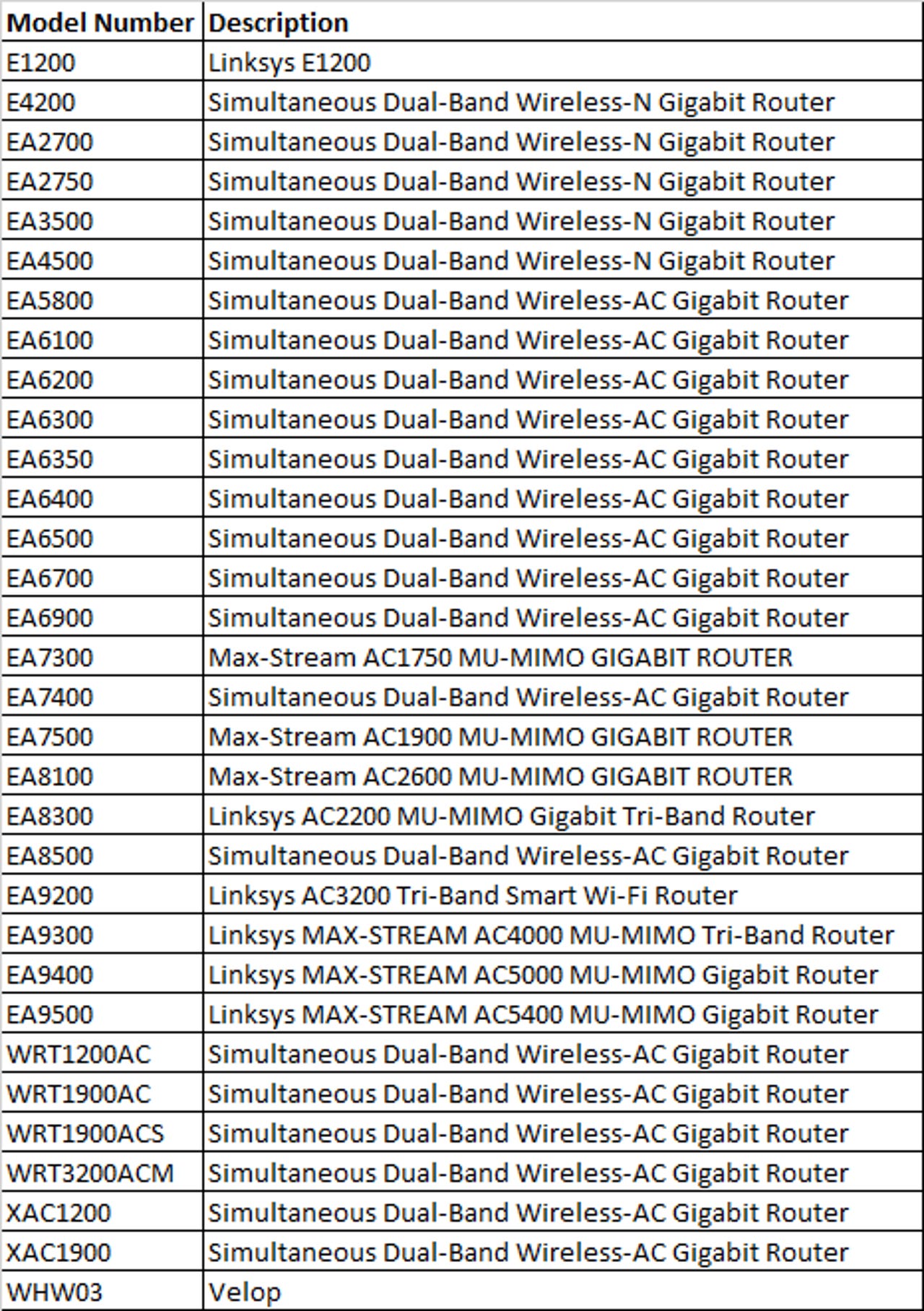
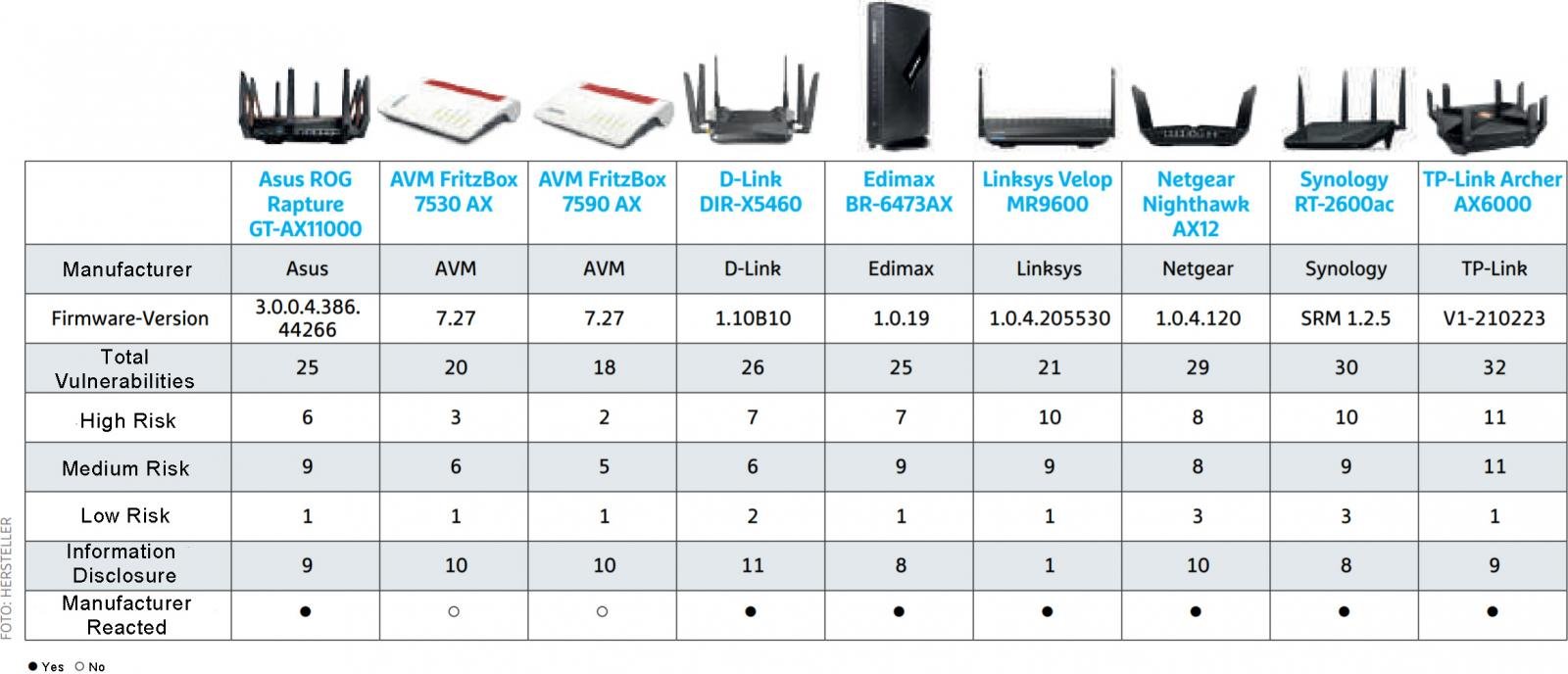
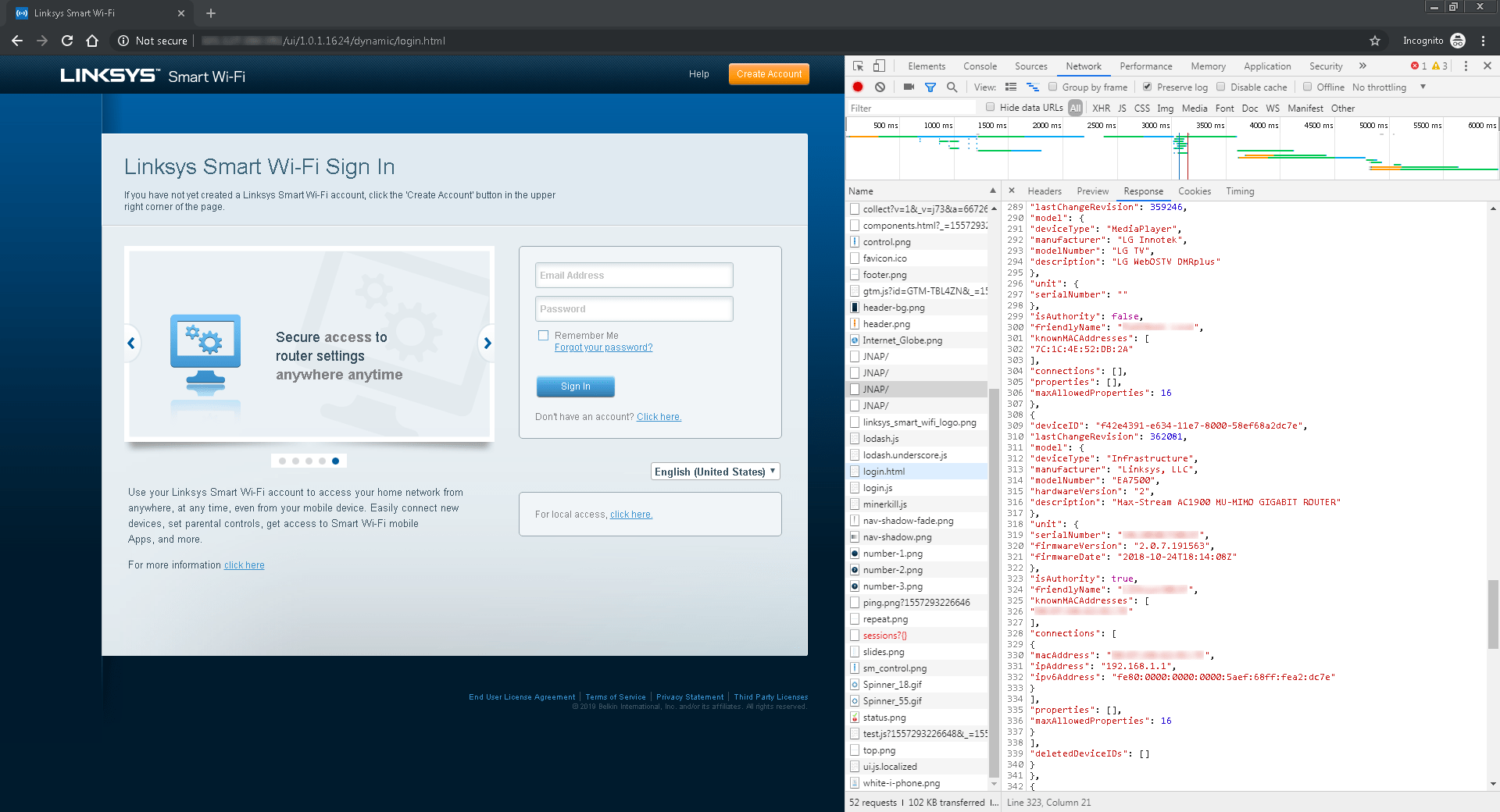
Got one of these Linksys Smart Wi-Fi routers? Bad news. 10 security vulnerabilities discovered • Graham Cluley